Numbers released from DTCC on Jun 4, 2024, (one week into the T+1 transition in North America) showed that Wall Street had just passed what many thought would be the toughest test of the accelerated T+1 regime. Key trade fail rates dropped in the first week of T+1 to 1.71%, compared to the daily averages of 2.24 under the T+2 system.
While T+1 settlement promises reduced trade failures and increased efficiency gains, it also tightens the window for detecting cyber threats, expanding the attack surface. What’s more concerning is how cyber threats in the securities trading sector are as varied as they are relentless—think phishing, email attacks, data breaches, identity fraud, and more.
While the SEC is going all out to ramp up scrutiny and security through versatile initiatives like:
- the Cyber Disclosure Rule of Sep 2023 (mandating publicly traded companies to notify them of a cyberattack within four days of the incident)
- The recent amendments to Regulation S-P (institutionalizing the need for a Comprehensive Incident Response Program to safeguard customer data),
The Burning Question Is: Have Brokers Kept Pace?
Operating with cybersecurity frameworks that follow a rinse-and-repeat approach, several brokerages have incident response plans as an afterthought, insufficiently integrated across their operations.
Equifax’s 2017 breach serves as a cautionary tale (personal details of 147.9 million U.S. consumers were compromised) for current industry players: It highlights gaping holes in the firm’s cybersecurity and risk mitigation strategies, particularly how an expired security certificate left encrypted traffic uninspected for ten months. This lapse allowed attackers to steal data, UNDETECTED.
In hindsight, a proactive approach with real-time data monitoring systems, regular audits, and automated systems with periodic alerts to renew security certificates could have averted the crisis.
How Can Brokers Prepare for Cyber Threats & Attacks in a T+1 Environment?
Brokerages that have successfully navigated the T+1 transition offer critical insights into robust incident management. Goldman Sachs has a multi-layered security approach that combines advanced analytics, continuous monitoring, and rapid response protocols. Its dedicated incident response team proactively conducts regular drills designed to closely mimic real-world conditions, ensuring that the team is adept at handling incidents.
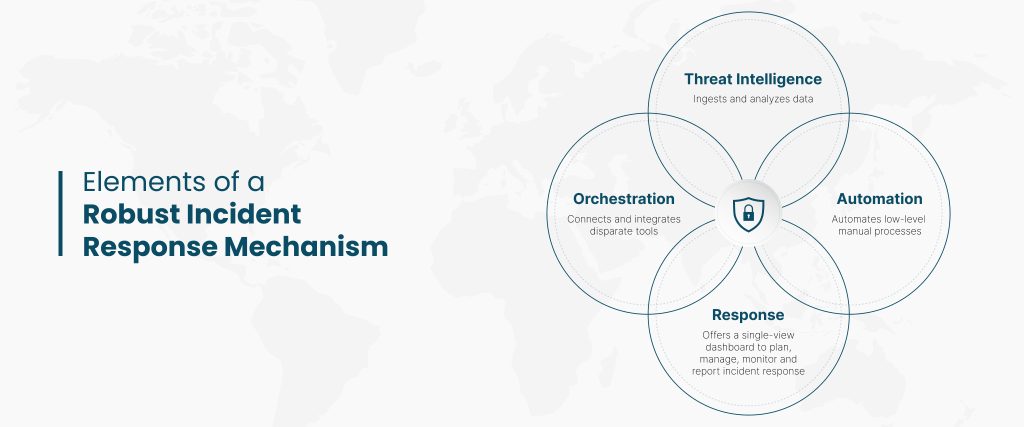
Building on such best practices, here are a few incident response strategies that can help brokerages:
- Advanced threat detection tools: A sophisticated incident response mechanism begins with advanced detection and prevention technologies. Leveraging AI and ML for minor improvements can be a good starting point, as they help automate data and draw patterns to identify and mitigate threats in real-time. Predictive analytics can sift through vast amounts of data to pinpoint unusual patterns that might indicate a breach. Sustainable technology practices, such as continuous system updates and adopting zero-trust architectures, ensure long-term security.
- Real-time data monitoring and integration: Robust integration capabilities that connect disparate systems offer a unified approach to incident response and minimize downtime during security incidents. A brokerage firm could integrate its security information and event management (SIEM) system with its core trading platform to provide real-time alerts and automated responses.
- User-centric design for heightened security: Designing user-friendly interfaces and clear visualizations can significantly enhance the efficiency of incident response teams. Developing a dashboard that provides real-time security alerts, visualizes threat levels, and guides response actions can streamline incident management.
- Education & awareness building: Regular training, comprehensive cyber-attack simulations, and fostering a culture of awareness is critical, too. A critical element often overlooked is the integration of these educational initiatives with real-time feedback and performance metrics. For example, after each simulation, detailed reports are provided to participants, highlighting areas of strength and pinpointing weaknesses.
Expert Take
Brokerages should aim to strike a fine balance between adopting sophisticated technological solutions and nurturing human preparedness for a comprehensive approach to incident management. Drawing parallels, this can be likened to preparing for a modern-day Y2K, where the goal is not just to survive but to thrive under conditions that demand near-zero downtime and heightened vigilance against disruptions.
Managing attack surfaces across all systems (cloud, on-premises, and third-party vendor systems) and integrating cybersecurity preparedness at every level—from the C-suite to the broader workforce—is critical. The ultimate objective is to enhance operational resilience. While making systems completely impenetrable is impossible, minimizing damage and managing everything in real-time is essential. A comprehensive approach combines advanced AI detection tools, real-time monitoring, and user-centric interfaces to strengthen defenses. Remember, you are only as strong as your weakest link!


